Is your digital life truly secure in this age of pervasive social media platforms? The unfortunate reality is that hacking on platforms like Instagram is a growing epidemic, with millions of users falling victim to cybercriminals each year. This article dives deep into the current state of Instagram security, exploring the vulnerabilities and offering essential guidance for safeguarding your account and your online identity.
Social networking sites, including giants such as Facebook, Twitter, and Instagram, have become integral to how we communicate, conduct business, and even perceive the world. Instagram, with its vast user base exceeding a billion active monthly users representing a significant portion of the global population is a particularly attractive target for malicious actors. Data from sources such as NordVPN suggest a concerning trend: approximately 13% of Americans have experienced Instagram account hijacking. This highlights the pervasive nature of the threat and the urgent need for vigilance.
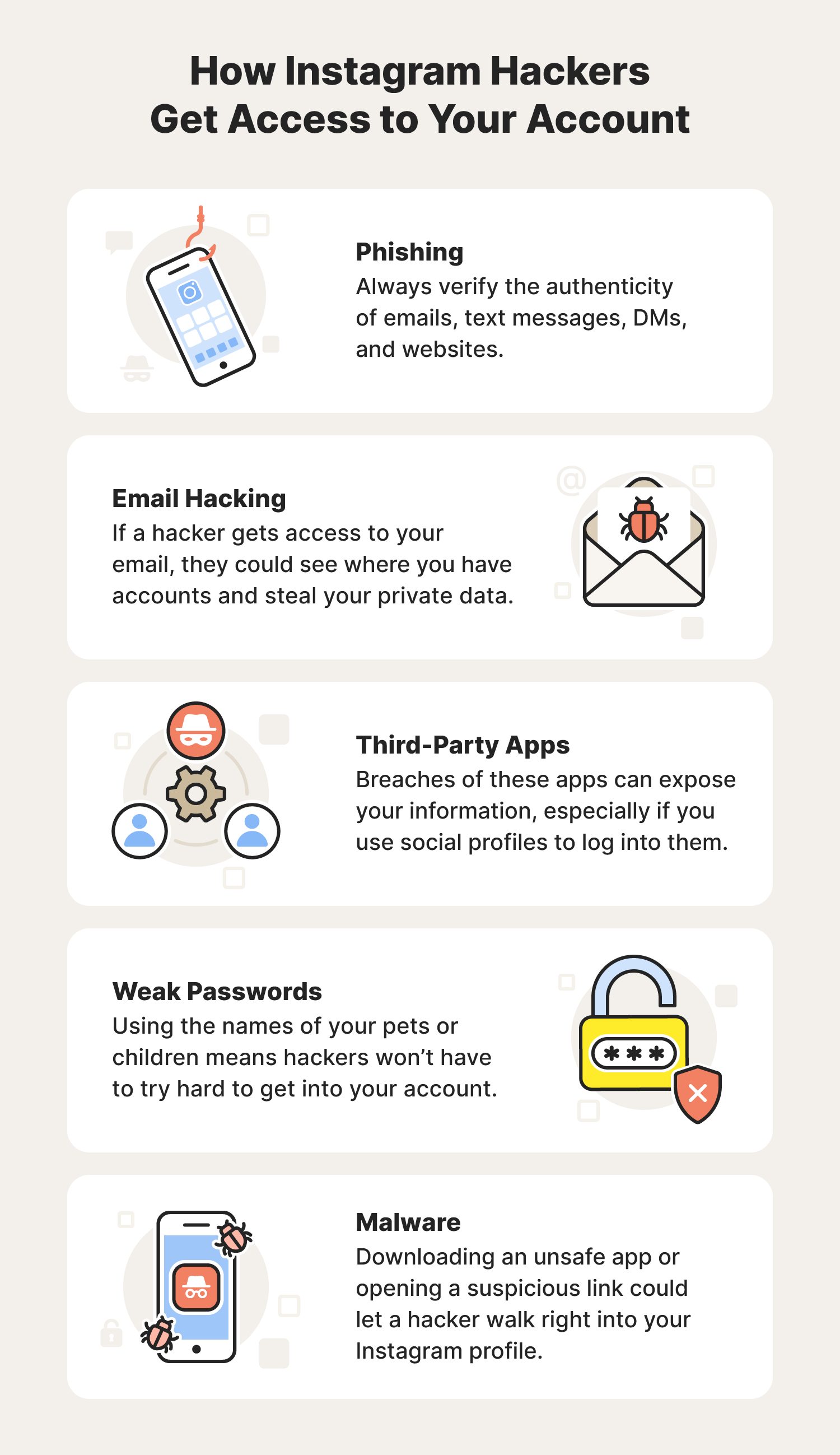
The methods employed by hackers are constantly evolving, ranging from sophisticated phishing attempts to leveraging simple human error. One of the most common tactics involves tricking users into divulging their login credentials. This often begins with a seemingly innocuous direct message (DM) from a "friend" requesting assistance with a password reset. Unwitting users, trusting the sender, may provide the one-time password (OTP) sent by Instagram, unwittingly handing over the keys to their account. Other threats include the use of third-party applications such as those claiming to track unfollowers that request your username and password, thereby gaining access to your account information.
Hackers are drawn to Instagram accounts because they can be used for a variety of malicious purposes. They can be used to spread misinformation, to scam other users, or to steal personal information. Once a hacker gains control of an account, they can change the account's profile information, post unwanted content, or send messages to the account's followers. The ramifications of such a breach can be devastating, causing financial losses, reputational damage, and emotional distress.
The good news is that there are proactive steps you can take to protect yourself. One of the first and most important steps is to understand the types of threats you face. For instance, a common misconception revolves around the idea of accessing a private Instagram profile without following the user. The truth, as confirmed by security experts, is that the only legitimate way to view a private profile is by following the account owner and being approved.
Instagram's settings include a wealth of personal information, including your name, email address, and phone number. A hacker will likely target this information first. The presence of a new security checkup feature on Instagram reflects the platform's effort to enhance user security. Another measure is reporting the hack to Instagram by following steps outlined in the "my instagram was hacked" link on the login page. Users are also advised to monitor their accounts frequently for unusual activity, such as changes to profile information or unauthorized posts.
The digital landscape is constantly shifting, and staying informed about the latest security threats is paramount. The costs associated with online security threats can be substantial, ranging from the direct monetary losses to the indirect costs, such as the time and resources needed to recover from an attack. According to research by Mutiyah, conducting a sophisticated attack on Instagram would require approximately 5,000 IP addresses, although even this scale of operation can be achieved at a relatively low cost, potentially around $150 if cloud providers like Google or Amazon are used.
In the face of rising cyber threats, it is always essential to employ strong, unique passwords. A password manager can be an invaluable tool for generating and storing complex passwords securely. Enabling two-factor authentication (2FA) is another critical step in securing your account. This adds an extra layer of protection by requiring a verification code from a trusted device or authentication app in addition to your password.
For those concerned about potential breaches, vigilance is important. If you cannot sign in to your account, consider it compromised. The hacker may have changed your password, logged you out, or even changed the email address associated with your account. In such a case, Instagram provides clear instructions on how to recover your account. You should immediately report the hack to Instagram and start the recovery process.
If you are monitoring the correspondence and chats of someone who is under 18 years old, living with you, and your legal responsibility as a parent or guardian, it is generally acceptable and within the bounds of parental responsibility. However, it is crucial to be aware of the legal ramifications, which can differ based on location and specific situations.
Furthermore, it is important to note that if your account has been breached and details such as your email address and phone number have been changed, you will need to follow the prescribed method through the Instagram help page. This is because your account's information is one of the primary targets for a hacker.
The prevalence of such attacks should encourage all social media users to take responsibility for their own online safety and be active participants in their online security. Keep an eye on your account for any unusual activity. According to Norton, a staggering one in six social media accounts will be compromised. Understanding and implementing these strategies is critical to navigating the digital landscape safely.
Here's a table outlining the common attack vectors and providing mitigation strategies:
| Attack Vector | Description | Mitigation Strategy |
|---|---|---|
| Phishing | Deceptive attempts to steal credentials through fake websites or messages. | Be cautious of suspicious links and messages. Verify the sender before entering any personal information. |
| Password Reset Scams | Hackers trick users into revealing their OTP during a password reset process. | Never share your OTP with anyone. Always access password reset options directly from Instagram. |
| Third-Party Apps | Unsecured apps requesting username and password to offer followers/analytics. | Use only trusted apps with strong privacy policies and positive user reviews. Be wary of apps asking for your credentials. |
| Account Takeover | Direct account breaches through stolen credentials, or exploited vulnerabilities. | Use strong, unique passwords. Enable two-factor authentication. |
| Profile Compromise | Unauthorized changes to profile details, posts, and other account settings. | Regularly review your account activity. Report any suspicious changes to Instagram immediately. |
This is a rapidly evolving field, and what works today may not be sufficient tomorrow. As technology advances and cybercriminals develop increasingly sophisticated tactics, it becomes critical to adapt and stay current with the latest best practices in online safety. The fight against digital threats is an ongoing battle, and knowledge is your most powerful weapon.
![How to Hack an Instagram Account in [year] (Password Hack Apps](https://increditools.com/wp-content/uploads/2022/09/xMobi-Instagram-Hacker.png)