Is your organization truly prepared for the relentless onslaught of cyber threats in today's digital landscape? Zero Trust Security, a paradigm shift in cybersecurity, is no longer a luxury but a necessity, and Zscaler stands at the forefront of this revolution.
The digital world has evolved at an unprecedented pace, transforming how businesses operate and interact. This evolution, while offering incredible opportunities, has also opened the door to a plethora of cybersecurity challenges. Traditional security models, built around the concept of a secure perimeter, are no longer sufficient. The rise of remote work, cloud computing, and mobile devices has blurred the lines, making it crucial to adopt a more agile and adaptable approach to security. Businesses are now increasingly judged on their IT outcomes, making cybersecurity a pivotal factor in their success or failure.
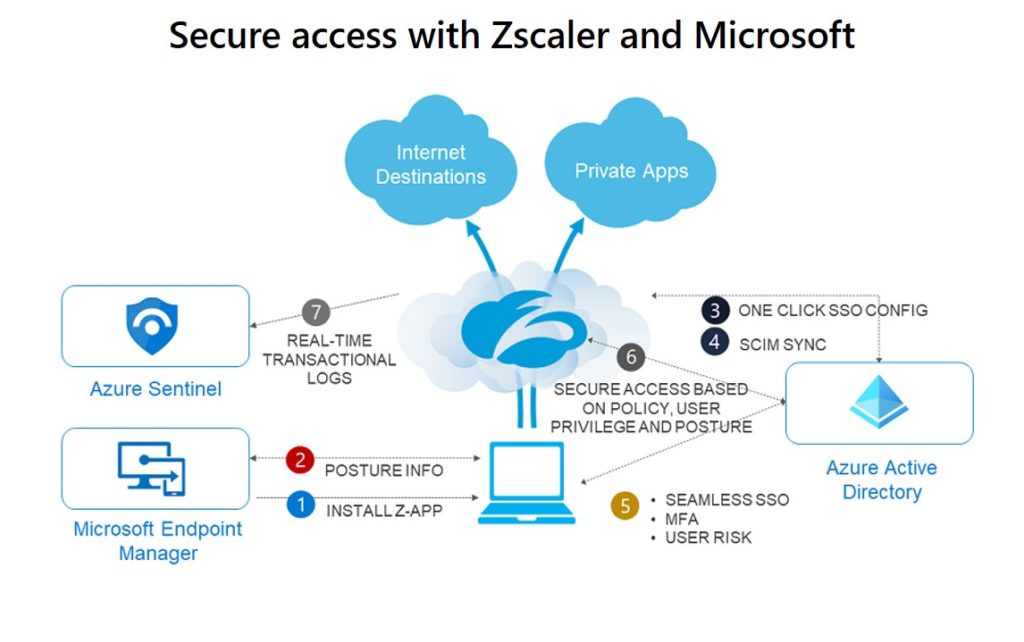
Zscaler, recognizing this shift, has built a comprehensive platform designed to meet the demands of the modern digital world. The company's mission is clear: to empower organizations to realize the full potential of the cloud and mobility by securely connecting users to applications from any device, anywhere. This mission is underpinned by a fundamental shift in how security is approached the Zero Trust architecture.
The core of Zscaler's solution lies in its innovative approach to network security. Zscaler Private Access (ZPA) acts as a connection broker, placing itself between clients and servers. This architecture has significant implications, primarily in safeguarding critical information. It hides real IP addresses from each other, effectively creating a layer of anonymity and preventing direct access to the network. Furthermore, ZPA mandates that every server connection goes through a login or Single Sign-On (SSO) process. This two-pronged approach drastically reduces the attack surface and enhances the security posture.
While ZPA and SSO are the major benefits of Zscaler, there are numerous features and functionalities, making it a comprehensive security platform.
Zscaler offers a cloud-native cybersecurity platform built on zero-trust architecture. This platform is designed to address the challenges of securing modern digital businesses, including those using cloud and mobile services.
Zscaler has built more than 100 data centers around the world which supports businesses to deliver their content without any delay, This vast global presence ensures that Zscaler can provide businesses with the performance and reliability they need.
Zscaler is universally recognized as the leader in zero trust, it leverages the largest security cloud on the planet, Zscaler anticipates, secures, and simplifies the experience of doing business for the world's most established companies.
Zscaler Privileged Remote Access (ZPA) is a valuable asset for organizations, enabling secure access to critical operational technology (OT) and industrial internet of things (IIoT) assets. Whether it's a field location, the factory floor, or any remote site, ZPA eliminates the need for VPNs or agents. This secure, direct access streamlines operations and enhances productivity. This functionality is critical for organizations looking to improve the efficiency and security of their remote access capabilities.
Zscaler distinguishes itself by being a cloud security solution designed with both flexible scalability and superior performance. It leverages a global network of data centers strategically distributed across all continents. This robust infrastructure enables the software to support businesses in delivering their content without delay, providing an optimal user experience.
Zscaler and CrowdStrike are two of the biggest names in the cybersecurity industry. However, their solutions are designed for different aspects of the security landscape. Zscaler is primarily a ZTNA (Zero Trust Network Access) solution that focuses on securing threats at the network layer. CrowdStrike, on the other hand, is an endpoint security solution that safeguards devices, applications, and data. While the functions of these two platforms differ, they often complement each other.
The Zscaler Zero Trust Exchange is a cloud native cybersecurity platform built on zero trust architecture. The Zero Trust Exchange is a complete platform that combines multiple security capabilities, including Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Data Loss Prevention (DLP), all delivered from the cloud.
If you're seeing a message about Javascript being disabled on your browser, it means that Javascript has been disabled. Please enable Javascript to make the app work.
The Zscaler approach recognizes that the traditional "trust but verify" model is no longer sufficient. Instead, it adopts a "never trust, always verify" approach. This means that every user, every device, and every application must be authenticated and authorized before being granted access to any resource. This significantly reduces the attack surface and limits the damage that can be caused by a breach.
By using Zscaler you can be rest assured that it has the ability to keep the confidentiality, integrity, and availability of sensitive data.